DO NOT OPEN THE “LEGAL” PAGE
lemmy.world is a victim of an XSS attack right now and the hacker simply injected a JavaScript redirection into the sidebar.
It appears the Lemmy backend does not escape HTML in the main sidebar. Not sure if this is also true for community sidebars.

EDIT:
the exploit is also in the tagline that appears on top of the main feed for status updates, like the following one for SDF Chatter:
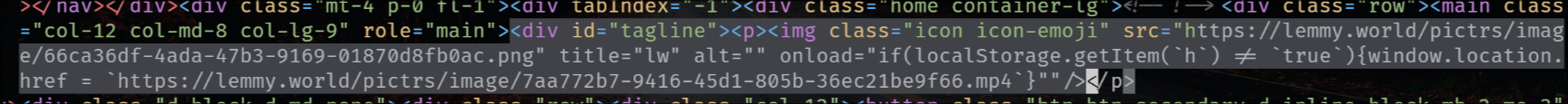
EDIT 2:
The legal information field also has that exploit, so that when you go to the “Legal” page it shows the HTML unescaped, but fortunately (for now) he’s using double-quotes.
"legal_information":" 


what about the time you wrote your “hello world” code? did you sanitize your user input then?
Simply having it Print “Hello World” without any user interaction? There are no user inputs to sanitize.
He sanitized the user input to the extreme by not allowing any.
The Apple school of thought
Best kind of correct
I mean if you’re gonna be making a literal english joke like this, then if there is no user input, then there is no user input to sanitize, which means no excuse is needed.
I follow and agree with your conclusion.
deleted by creator
“Listen here you little…”
Little Bobby Tables it is.